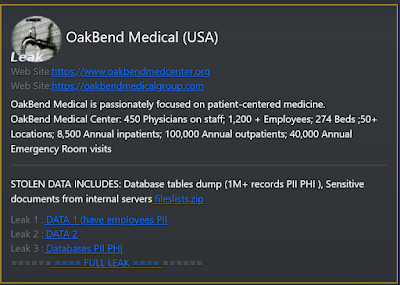
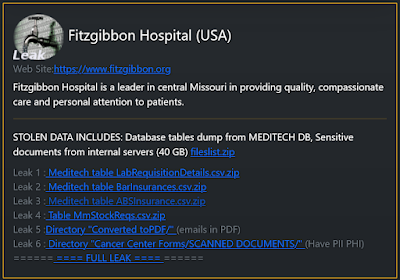
Wednesday, May 31, 2023
Cracking the Connected Floor
Sunday, April 23, 2023
Top 10 All Time Active Ransomware Groups
The Current Top 10 Active Ransomware Group Post Count
By Dominic Alvieri
April 23rd, 2023
Quantifying ransomware group activity over the past few years there is no doubt that LockBit is the numerical leader all credibility issues aside. LockBit averages posting over one company per day since their initial formation as ABCD. No one else comes close.
Conti members are still around but this list comprises of active groups with quantifiable active leak sites.
Posts that are somewhat quantifiable...
Up and Coming Groups
New groups in 2023
Most Dangerous Groups
Friday, March 17, 2023
SpaceX Contractor Allegedly Breached
LockBit leaves a message for Elon Musk
LockBit message to Elon in the post below.
What is it worth?
Mutual non-disclosure agreement
What happens when a ransomware group discloses an NDA?
Monday, February 27, 2023
Who Hacked Atlassian?
The Wolf in Sheep's Clothing
Ghosts of SeigedSec
 |
| Story by Carley Page and Zack Whittaker |
Where did SiegedSec come from?
 |
| The Wolf in Furry Hacker Clothing |
The Wolf in Furry Clothing
The leader of the new pack
The questions I wanted to know that I can share...
SiegedSec will be posting on their own Telegram channel
A-Yes
GhostSec
GhostSec Seb
Friday, February 3, 2023
I Can Name That Exploit in One Note
Another New Day and Another New Way...
Redacted
Monday, January 30, 2023
Undisputed LockBit
LockBit is clearly the leading group left standing...for now.
By Dominic Alvieri
January 30th, 2023
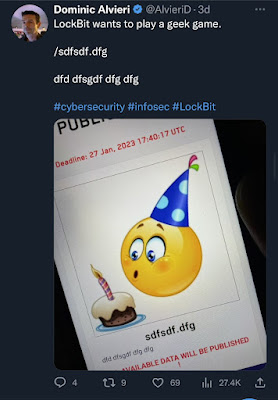
In the early morning hours of Thursday, January 26th a multi-governmental offensive seized the Hive Ransomware leak site. No arrests have been made in the never ending ransomware whack-a-mole game. LockBit is now the undisputed leading ransomware operation.
That evening LockBit was ready with a new game, comments and plenty of leaks ready to go. The Hive Ransomware leak site was seized early Thursday morning and the first comment or post from LockBit was a freaking game below.
The post above was removed by LockBit. Researchers at VX Underground were able to get a comment from Mr. LockBit about the post and the news that followed. LockBit is one group I do not have communications with and do not care to.
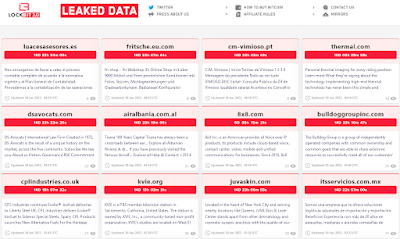
By Sunday evening it was business as usual as LockBit posted affiliate offerings of 14 new victims not willing to pay them from around the world.
Spain
France
Mexico
Austria
Albania
Portugal
Australia
United States
United Kingdom
Low lights from the new posts include PBS member television station KVIE in Sacramento, California, Air Albania, CPL Industries...
LockBit is clearly the top operation remaining and is arrogantly making it known. Alphv Black Cat Ransomware is behind LockBit and there is a clear distinction from the remaining groups including new up and coming Play Ransomware, Black Basta, Vice Society...
Several other groups and former members are not included in this article including Black Matter, DarkSide and the other variations, spinoffs and new groups pending like Endurance Ransomware.
No Hive arrests to date.
Affiliates have to go somewhere...
The never ending ransomware whack-a-mole game continues in 2023.
The Cyber Show
Tuesday, December 20, 2022
2022 Year in Rear View
The Increasing Rise of Ransomware and Security Fails in Rear View
Biggest Security Risk?
Vice Society Did Not Create Their Alternate Black Logo
Did Vice Society Breach a US Hospital in November?
 |
| Vice Society did not create this alternate white logo either. @AlvieriD |
The Trillion Dollar Expense?
FBI reports place a hard number on the problem
Just a Few General Trends for 2023
 |
| Ragnar Locker posted Serena Hotels |
Tracking an APT or group?
Remember Some Lapsus$ Members are Still Around
The Kremlin, Politics and Ransomware
Qilin Ransomware caught with politically motivated fake document (and old data) in post. by Dominic Alvieri March 8th, 2025 @AlvieriD Was it...

-
Did Black Suit Ransomware just try to troll me? by Dominic Alvieri July 3rd, 2024 @AlvieriD The story goes a little something like this... ...
-
Qilin Ransomware caught with politically motivated fake document (and old data) in post. by Dominic Alvieri March 8th, 2025 @AlvieriD Was it...
-
Annoying drones invading your private property? By Dominic Alvieri December 25th, 2024 @AlvieriD Hacking is Illegal and for Nerds Stopping a...