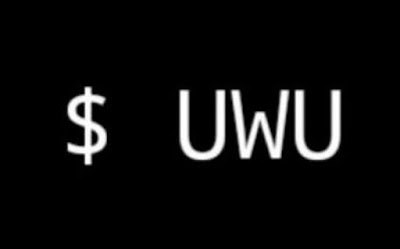The Wolf in Sheep's Clothing
Ghosts of SeigedSec
By Dominic Alvieri
February 22nd, 2023
One of the largest companies breached to date this year was carried out by a relatively unknown group, SiegedSec. "Little is known about the Hacking Crew" an analyst said as Envoy and Atlassian blamed each other initially last week. I had questions so I decided to reach out.
The SiegedSec Hacking crew?
 |
| Story by Carley Page and Zack Whittaker |
Where did SiegedSec come from?
The leader of the new group called SiegedSec likes to be called Wolf and he came from and still is a member of GhostSec. The leader of GhostSec goes by Seb. Why the separate group? That was one of my first questions besides "the Furry Hackers" comments.
The Wolf in Furry Hacker Clothing insists on maintaining the controversial furry angle through the conversations and updates. Personally I think it is an act to draw attention to important matters like freedoms which have been curtailed all across the globe in the past few years.
It is tough to take this seriously and I have no idea how long it will last but neither group is leaving the scene anytime soon. Hacking Atlassian no matter how will still draw attention to whatever your cause is. This feels like an attempt to capitalize on a situation which other groups have tried to make a huge splash and then pivoting from that initial buzz into the actual or real group.
 |
| The Wolf in Furry Hacker Clothing |
The Wolf in Furry Clothing
The leader of the new pack
Making a splash after a controversial United States Supreme Court decision last year, little known SiegedSec is back with a breach of giant Atlassian. I caught up with GhostSec to ask why the post was released through their channel and continued to drill down,
Here are some of the specific questions asked and answered over this past week.
Q-Who is SiegedSec?
A-Seb (GhostSec) SiegedSec was one of my members who decided to do his own thing. He still is a member of GhostSec as well.
Q-Still a member?
A-Yes.
The questions I wanted to know that I can share...
Q-Wolf-The state hacks last year...and why active again now?
A-...not as easy as it seems to quit hacking. That's the way I would put it, hat's why SiegedSec came back
Q-How did you breach Atlassian?
A-Honestly answered and redacted for security and breach confirmed by Atlassian.
Q-Was Atlassian a target?
A-No...
Q-Did you ask Atlassian for a ransom or was it just for shits and giggles?
A-Just for shits and giggles
Q-Any other victims or lateral movement?
A-No answer or evidence was provided.
SiegedSec will be posting on their own Telegram channel
To both Seb and Wolf
Q-Did either of you breach anyone this week?
A-Both "No comment."
I got the feeling that they both may have.
Q-Wolf or Seb, Is the UWU what I think it is along with the "Furry Hackers"
A-Yes
UWU is slang and loosely described a furry loving or friendly. Lets leave that be for now.
Throughout Wolf insisted upon being and going with the Furry Hacker theme.
Anything SiegedSec wants to say? Shortened answer
"Just represent yourself and be yourself, be a furry hacker who cares."
GhostSec
Leaving out the basic get-to-know-you hacker exploit talk and the like, I asked questions to both like is either group thinking of setting up a leak site.
Both have thought about it but not now in the works, at least not officially.
Speaking with Seb from GhostSec he struck me as being honest in answering my questions of which I already knew some of the answers. I obviously cannot release some questions asked and answered here but might be conversed...
qqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqq
...at a bar and not online.
GhostSec Seb
Q-Why Maine?
A-We have nothing against the State of Maine of their people we just happened to breach them.
Q-Any specific targets or breaches you can share?
A-Not at the moment.
Q-What are the odds that LockBit or Black Cat will post while we are chatting?
A-Highly likely lol
LockBit did post a company during the interview.
Q-I wish I could post more of this conversation, Do you have a statement?
A-Shortened Answer-Hack the Planet, if there is no path, create it. Fight against injustice.
Stay safe
Dominic Alvieri
Twitter @AlvieriD