The Increasing Rise of Ransomware and Security Fails in Rear View
By Dominic Alvieri
December 12th, 2022
What a year. Cisco, Microsoft and nearly every other company it seems was attacked this year. Rackspace and Uber are in the news again in December for all of the wrong reasons, A former Lapsus hacker allegedly hacked Uber, again. LockBit allegedly breached the Italian Tax Revenue Agency, L'Agenzia delle Entrate again, Vice Society allegedly breached a college again etc.
A new ransomware group war is brewing as Royal Ransomware backdated a post for Mark-Taylor, an Arizona builder dated December 13th that Hive Ransomware posted on December 14th.
Play Ransomware posted H Hotels, Ragnar Locker posted Serena Hotels and Royal Ransomware also posted a small hotel attempting to show that they belong.
New ransomware groups and leak sites have sprung up but no major leaks yet so no need for any mentions, yet. Play Ransomware is an up and coming group in my opinion and looks to be an offshoot of or similar to another group.
Biggest Security Risk?
Make sure you know who owns your instance, for instance. There are so many security risks that is probably going to be the mandatory monthly blog for January along with a few interesting updates.
Vice Society Did Not Create Their Alternate Black Logo
Vice Society did not create their alternate black logo, I did. I just changed the background colors when Vice Society posted their new logo on their leak site before I reported it on Twitter. I like the purple logo but think the black stands out more. Mystery solved.
Did Vice Society Breach a US Hospital in November?
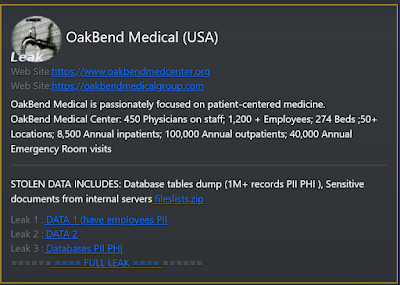
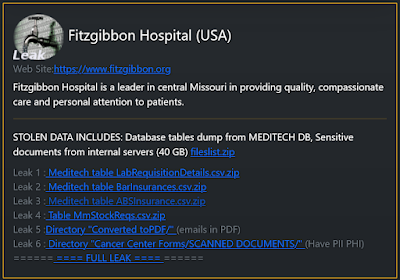
No, not to my knowledge. I have been in contact with a few employees of two hospitals breached, one of which has been able to confirm some attributing details needed to confirm the incident from the outside the investigation. The Daixin Team breached at least one hospital in the United States and verified it through an employee who did not wish to go on record. These hospitals are in addition to the OakBend Medical and Fitzgibbon Hospital breaches posted this year. The new confirmation includes the encrypted extension attributed to Daixin. I am not disclosing the hospitals which have disclosed the cyber incidents but did not report the group responsible.
The new breach timeline is between their OakBend Medical and AirAsia leak posts in November.
The hospitals in question might still be within the ransom negotiation stage or cyber insurance payment stage which I am not going to interrupt.
 |
| Vice Society did not create this alternate white logo either. @AlvieriD |
Vice Society alone this week allegedly breached The Catholic University of Portugal, the University Institute of Technology of Paris and Xavier University of Louisiana, XULA and not Xavier of Ohio.
Hive Ransomware posted the City of Huntsville, Texas, Interface, North Idaho College, Dixons Allerton Academy, Innovative Education Management, Stolle Machinery, and JAKKS.
LockBit posted over a dozen companies today. Ragnar Locker, Cuba, Alphv Black Cat and others posted a few days before Christmas as all the ransomware groups were looking to get paid before the start of the new calender year.
Some group disbanded while others expanded. Affiliates came and went, again.
The year is expected to break most if not all cybersecurity breach and ransomware records and certain trends are very noticeable.
The Trillion Dollar Expense?
The sad fact is that cybersecurity does not produce revenue and is not what corporations like to spend money on. Contest that statement if you wish.
It is difficult to place a financial number on the ransomware payment problem and it is more of an art than a science but it is easy to see that it is way over a billion dollars. Hive and Cuba Ransomware alone combine for over $160 million. Cuba Ransomware did even better on a percentage per victim, a metric some groups strive to maximize along with getting the most amount of money they can.
c/o Bleeping Computer, Sergiu Gatlan
FBI reports place a hard number on the problem
Just a Few General Trends for 2023
Expect more ransomware groups to show up on the scene. More new malware strains as well.
Expecting more re-breaches in 2023 of companies that were breached in 2022. Difficult economic times will cause some groups to attack previous targets at a faster rate. This is not a new tactic.
Predicting more and more simultaneous multi-group breaches to come. In the last few weeks both the Kenosha Unified School District and Mark-Taylor have had at least two groups allegedly breach them at the same time. RansomHouse and LockBit affiliates have been accused of the same.
The last two months of the year saw Quantum list a Wall Street floor broker, Black Basta post a small US bank and Royal Ransomware allegedly just breached a full service commodities broker today.. Expect the trend in financial firm ransoms to continue despite the added risks. That is where the money is.
Attribution will become more difficult. Builder leaks for one are making attribution more difficult.
Infrastructure turnaround times are decreasing from my research in some instances within 72 hours during this print. An alleged LockBit infrastructure has already been dismantled and restarted.
 |
| Ragnar Locker posted Serena Hotels |
Not every ransomware gang or group has affiliates. Expect that trend to fade. Economic conditions are also to blame as is a failing crypto ecosystem that is ripe with fraud. Quiet news this week has Armanino leaving the crypto accounting world as is Mazars, the accounting firm that handles Binance which was reported by Accounting Today magazine on December 17th.
If Bitcoin, Monero and the like continue to fall the ransomware groups will just continue to raise the dollar amount they ask for. Don't think that the groups don't monitor crypto and stock prices and outlooks. They are running a business.
Expect ransomware activity and ransoms to rise. It is not a set Bitcoin ransom it is a set dollar ransom.
Intermittent encryption is continuing its rise in popularity now and is being used by Alphv Black Cat, Hive and Play Ransomware among others. Expect this trend to continue to rise.
Tracking an APT or group?
Tracing and tracking ransomware groups and APTs isn't for the faint of heart. There will always be a digital forensic trail no matter how much you try to hide and obfuscate it. APT and ransomware group infrastructure changes quickly, at least the good ones do. Obviously I can't reveal all the tricks of my trade but tracking certificates is one way to track group infrastructure.
Remember Some Lapsus$ Members are Still Around
Even though ransomware groups like Lapsus$ and Karakurt would love to have me work with them I prefer to work with Cisco and Microsoft. Sorry fam, still love ya! I lost count of how many groups I spoke with this year. Not sure why so many groups reached out to me, hackers code I guess. A good hacker respects another good hacker. Most analysts and reporters aren't very good crackers. Some analysts may know some pentesting techniques which I believe are not as effective if you don't get to use them since most pentrests leave serious security gaps when testing with so many assets out of scope.
Lapsus$, Karakurt and a few others even reached out to me on Twitter. Non public conversations are just that, not public so I don't post or report anything without consent. I do not aspire to be a reporter so no worries there guys.
I do not work for or am an affiliate of LockBit, Lapsus$, Black Cat, Karakurt or any other group.
Dominic Alvieri
Twitter AlvieriD
AlvieriD@infosec.exchange














No comments:
Post a Comment