Telegram Channels are Behind Evil New Ways to Separate You From Your Money
By Dominic Alvieri
2-22-2022
Telegram has had a history of security breaches, bad actors and security issues for several years. More and more malicious actors are using the platform along with 300 million others. Recent examples during the Russian invasion of Ukraine are showing an accelerating trend of cyber activities on the platform including the SberBank breach disclosed below.
Other recent troubling requests
The Telegram mobile protocol MTProto protocol is proprietary and has had security questions for years. Cryptographic issues aside the desktop version does not use the protocol and storers all data in plain text. Plain text is also an issue with the mobile virtual cloud set up.
In simplistic terms all data is stored on Telegram servers and not end to end encrypted (e2ee) by default. There is a secret chat option that does but that is another story. No e2ee by default leaves millions at risk from an advanced attacker.
The current state of the gram
Underground forums and marketplaces are nothing new for a bad actor looking to score some low grade malware, stolen credit cards or a phishing kit. No need to fire up the TOR browser now because these items are becoming more mainstream available on the web and malicious Telegram channels.
OTP 2FA password stealing bots are being packaged with hand selected robocall features like foreign language accents to target customers of specific countries. Two if these bot services have been verified as working account stealing bots and recent reports of usage and abuse has been reported.
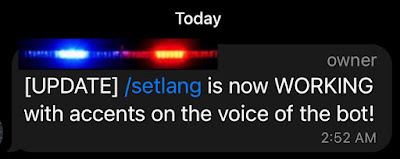
New set language feature /setlang
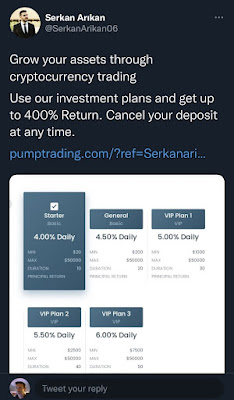
Bank of America, Chase and Wells Fargo are among the banks that these bots works with stealing your one time password or 2FA login. Several cryptocurrency platforms are also being marketed with automated bots and classes.
Several channels are selling various One Time Password (OTP) and 2FA stealing bots. Having verified two of the products here is a breakdown of some of the malicious capabilities.
Packages are readily available for Apple Pay, banks, crypto....
Vendor P above has been active in advancing the bots attack capabilities in the past week adding Bank of America and Chase to their hackable list. Security support teams at Bank of America, Chase and Telegram have been notified.
Here is what the bot can do. The ability to go after anyone with just the minimum information that would be needed to carry out this attack is worrisome. Basic OSINT research.
As simple and annoying as this scam is the technology behind the maliciousness does work.
Enter target data, select a few options and assets to acquire and the nightmare scenario begins. Like most malicious activities they do require at least one action from the target, barring a zero-day, zero click exploit.
Video snapshot of working bot in action
Robocalls blanket the target with messages of an account breach and that verification is needed. An extreme sense of urgency is created and conveyed in the robocall accent of your choice. The artificially curated voices of the bot repeatedly mention your account is at risk and require you to verify your account via an OTP or your 2FA verification.
Partially redacted for security.
Everything is the same as before...
We have come along way from just unlocking iPhones.
What else can this bot do?
New functions which have just been posted and untested include bypassing:
-Authy
-Google Authenticator
-Microsoft Authenticator
Several variations of the original bot are online and to no surprise many claims are stretched and many are just outright frauds.
Relentless requests are the first step and if entered, the near-instant theft takes place. When a verification code is entered the bot executes the code, enters the account and transfers all of the cash or cryptocurrencies out of the account within minutes. In this live research example a crypto account was used and emptied within 2 minutes of the final string of data obtained by the bot. Crypto firm name withheld.
Several other options are available if the first level attempt via robocalls fail to capture the required codes. These are actual working multifaceted bots able to spear or whale nearly anyone.
What can you do? DO NOT INTERACT
Do not interact with any SMS, email, link or call regarding your breached accounts. Always go directly to your real account through and official site or representative.
Go directly to any account in question and the official site and or contacts and avoid any "urgent need" to give your information to anyone. Chances are you haven't been hacked but someone sure is trying.
The Cyber Show
by Dominic Alvieri
Twitter @AlvieriD